Security researchers have unearthed a new threat vector for Google Chrome that tricks users into downloading a ‘missing font’ and subsequently installs a malware on their system.The trick was spotted first by Mahmoud Al-Qudsi, a security expert from NeoSmart Technologies while browsing an unnamed WordPress website was allegedly compromised already by the hackers. However, the attack was well disguised. The hackers had deployed JavaScript to tamper with the text rendering thereby causing the miscoded text to be resembled in place of actual content. Thereafter, the users are prompted by the script to install the missing Chrome font pack.
![]()
The sophistication of attack lies in the subtle threat vector employed by it. Apart from the missing font premise that looks credible, the dialog window has been professionally formatted to resemble an actual Chrome pop-up. The logo and the color used are actual ones.
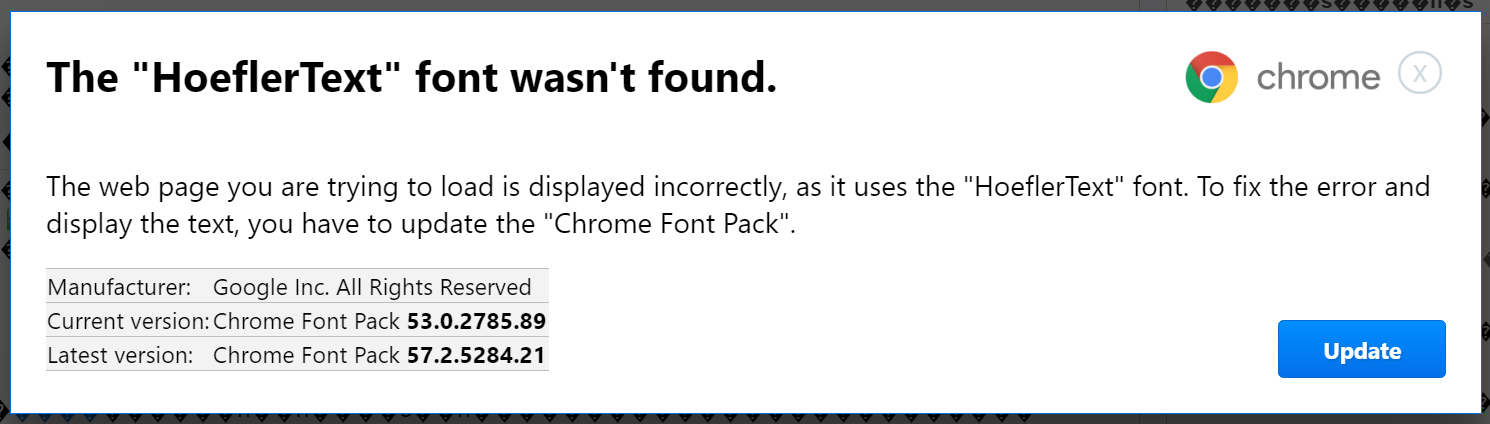
As per the security firm, the users can figure out the malicious activity by carefully spotting some signs. First, the dialog window is hard-coded to tell that version 53 of Chrome is being run by the user. If the user is running a different version, the hack could be arrested in the first place itself. Secondly, the name of the download file displayed in the instruction image is Chrome_Font.exe which is different from the one that is actually downloaded and goes by the name Chrome Font v7.5.1.exe.
However, the users need to be careful with these signs if they intend to not fall prey to this hacking. This is because both Chrome and Windows Defender fail to filter out the file as malware and label it as malicious respectively. The security firm performed a precautionary scan through VirusTotal which revealed that only 9 out of 59 anti-virus software were able to accurately identify the file as malicious.

Publisher









/https://cystory-images.s3.amazonaws.com/shutterstock_534572380.jpg)
/https://cystory-images.s3.amazonaws.com/shutterstock_434415385.jpg)
