Barely 50 days have passed since the WannaCry ransomware attack that paralyzed organizations in more than 100 countries, and now a new variant of Petya ransomware has struck across the globe infecting firms in different countries. As of now, the majority of the attack burden lies in Europe where several multinational companies spanning different sectors have been infected. As per preliminary reports, the victims include government banks, state electricity grid, telephone companies in Ukraine. The attack has disrupted functioning in various multinational companies like Saint-Gobain, Russian steel magnate Evraz and Rosneft, France’s Saint-Gobain and Danish shipping company AP Moller-Maersk.
According to a statement released by the central bank of Ukraine, the attacks have caused serious disruptions in the banking services and rendered it difficult for client servicing and day to day banking operations. The central bank has attributed the attack to an unknown virus. However, as per security experts from Kaspersky, the attack has been carried out using a new variant of Petya ransomware also known as Petrwrap. The new variant has been observed in the wild since June 18 and is now spreading at an alarming rate. This new attack has infected organizations spanning across entire sectoral spectrum including power grids, gas stations, airports, banks and bus stations. There are reports of infections coming from the USA, India and Spain.
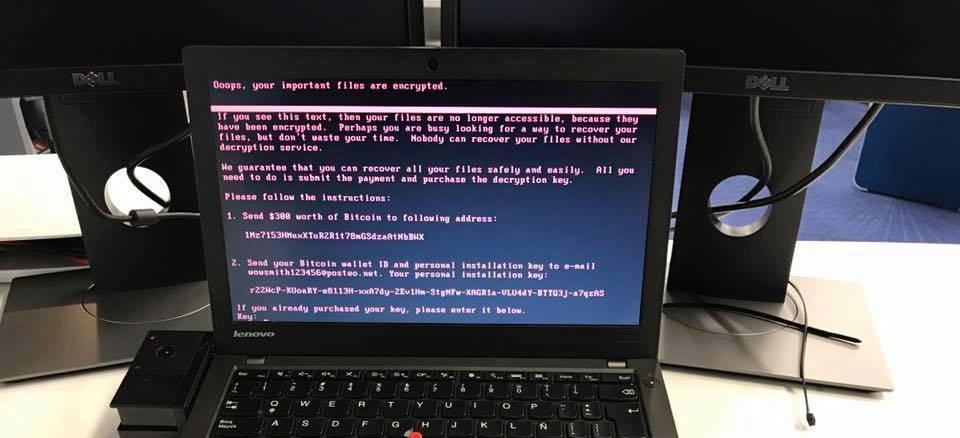
As of now, the complete picture regarding the vulnerability exploited and the threat actor behind the attacks has not emerged. However, some experts have said that Petya is exploiting the same vulnerability (EternalBlue) that was exploited by WannaCry ransomware and has a wormy nature which makes it spread over a network from an infected computer. As per Virus Total only 15 out of 62 antivirus software are able to detect this new variant of Petya as of now.
The users are strongly advised to take the following proactive measures to protect their systems from getting infected:
- Update your Windows: Microsoft has already patched EternalBlue vulnerability for the supported versions of Windows. Although, it is not yet fully clear if the Petya is exploiting this vulnerability but users must keep their Windows updated as a precautionary measure. For, the versions of the Windows like XP, Windows 8 and Windows Server 2003, that receive only custom support, Microsoft has previously released a new security patch.
- Disable Server Message Block (SMB): Microsoft has released a detailed guideline to disable Server Message Block (SMB).
- Block access to these ports: Users must block access to SMB ports over the network. The protocol operates on UDP ports 137 and 138, TCP ports 137, 139, and 445. Users must modify the configurations in the enabled firewall settings to perform the same.
- Backup your data: It is strongly recommended that users must maintain data backup to have a work around in case their system gets infected and not create an unwarranted situation where they have to pay ransom to get back their sensitive data. Moreover, there is no guarantee that the hackers would return back the data even after making ransom payment.
- Cyber Situational Awareness: The users must remain updated on the latest developments regarding Petya and take measures as suggested. Every firm needs to empower and make their organization cyber aware and cyber hygenic through situational awareness and incident reporting platform.Security First culture is the need of the hour and the only way forward to proactively mitigate cyber risk.
Watch out this blog for latest developments on Petya ransomware attacks and remain updated.

Publisher









/https://cystory-images.s3.amazonaws.com/shutterstock_276804236.jpg)
/https://cystory-images.s3.amazonaws.com/shutterstock_546873682.jpg)
