Outpace Threats with Agentic AI-Powered Threat Intelligence Management
Secure your organization with our unified, fully integrated AI-powered Threat Intelligence Platform that operationalizes threat intelligence in real time.
“Threat intelligence has become an established pillar of security operations, evolving beyond SOC use cases to support enterprise-wide objectives through multisource integration, AI-driven analysis and preemptive capabilities to combat evolving global cyberthreats.” — Gartner Threat Intelligence Report
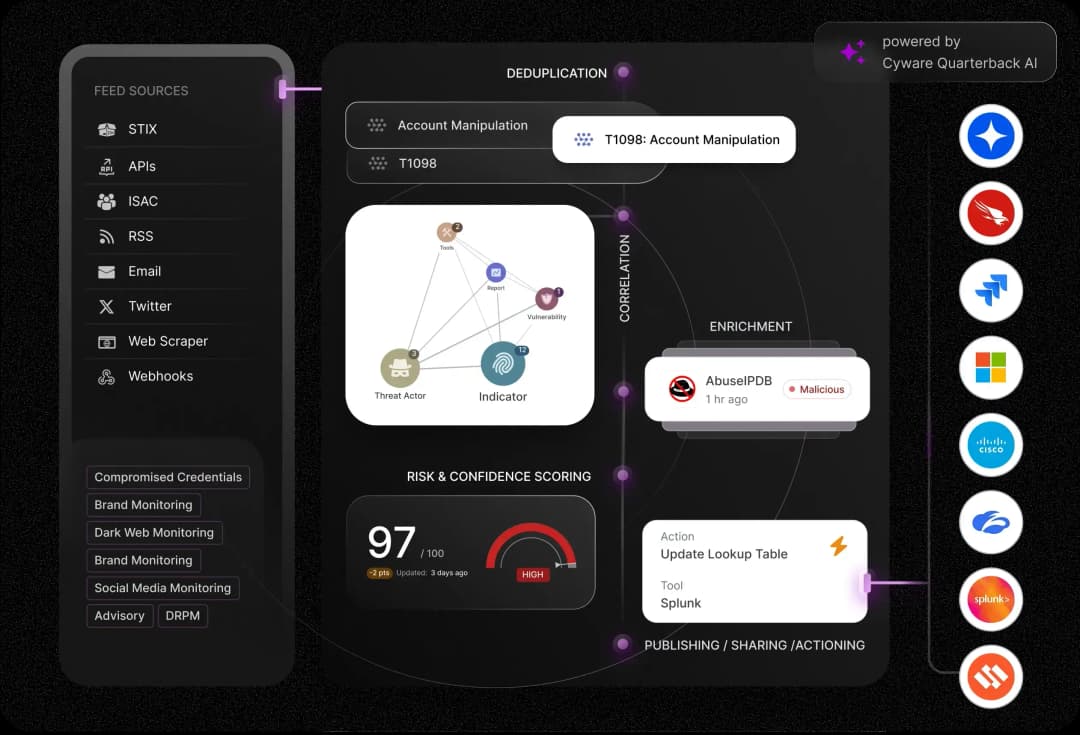
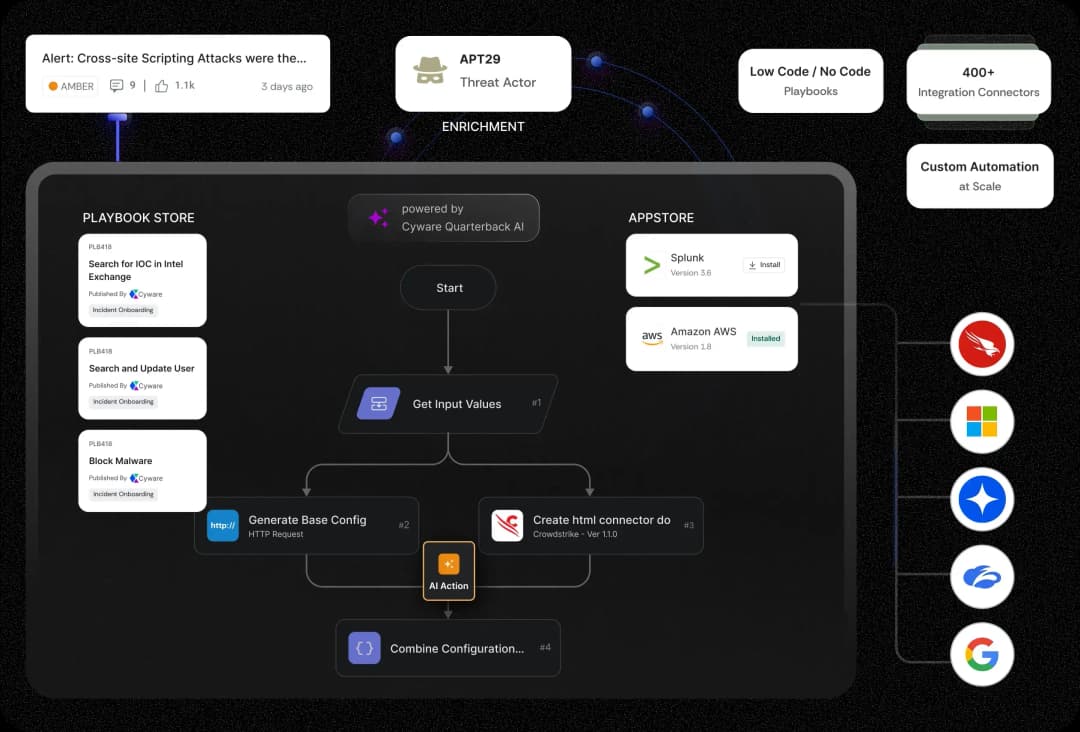
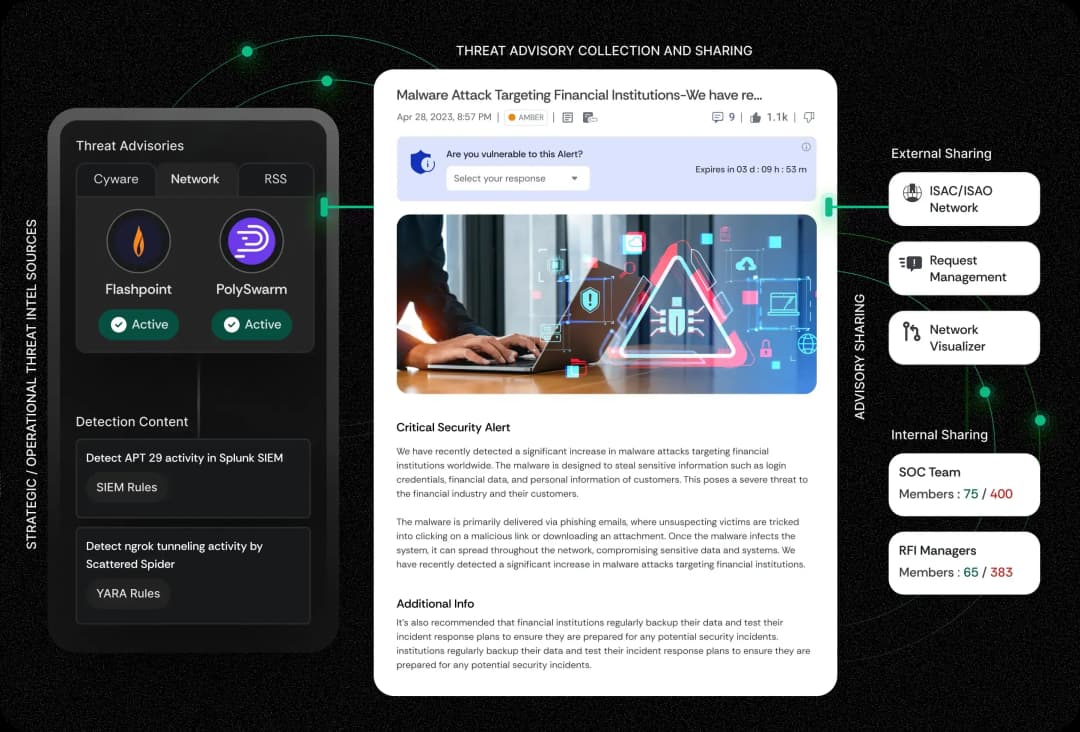
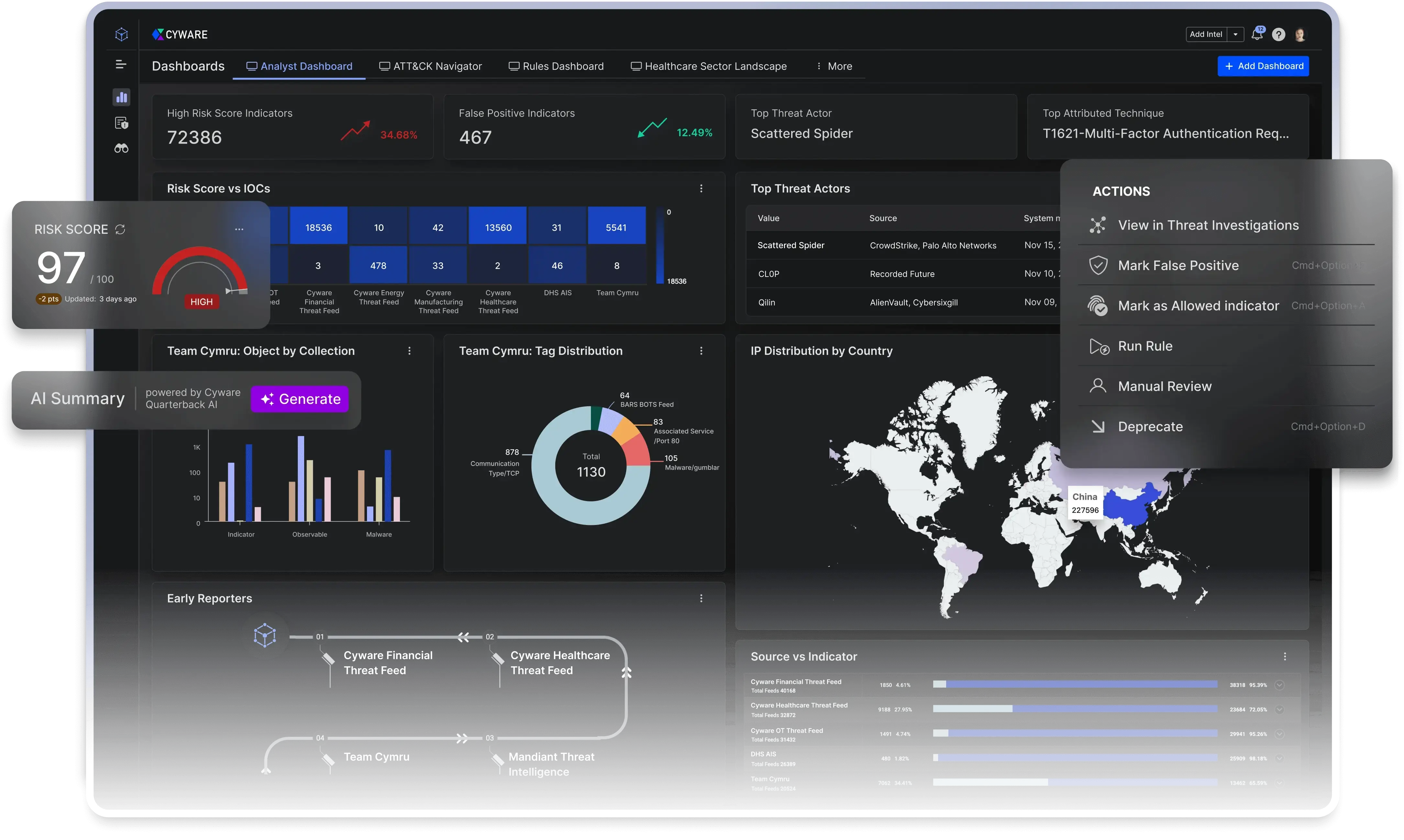
Operationalize Threat Intelligence and Strengthen Collective Defense with AI-Powered Threat Intelligence Management
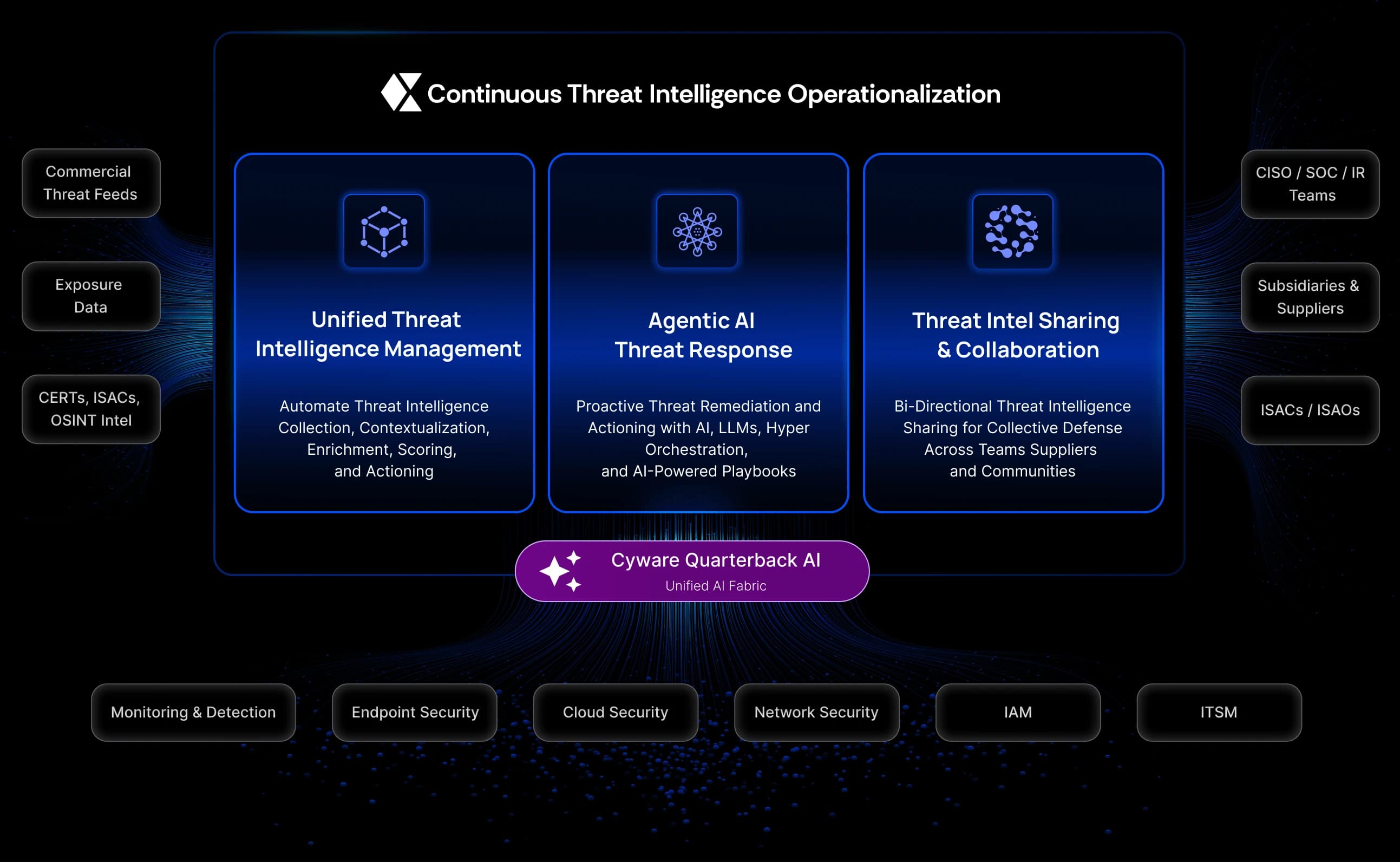
See, Act, and Share Threat Intelligence to Strengthen SecOps
Accelerate threat detection, simplify investigations, streamline response, and enhance collaboration.
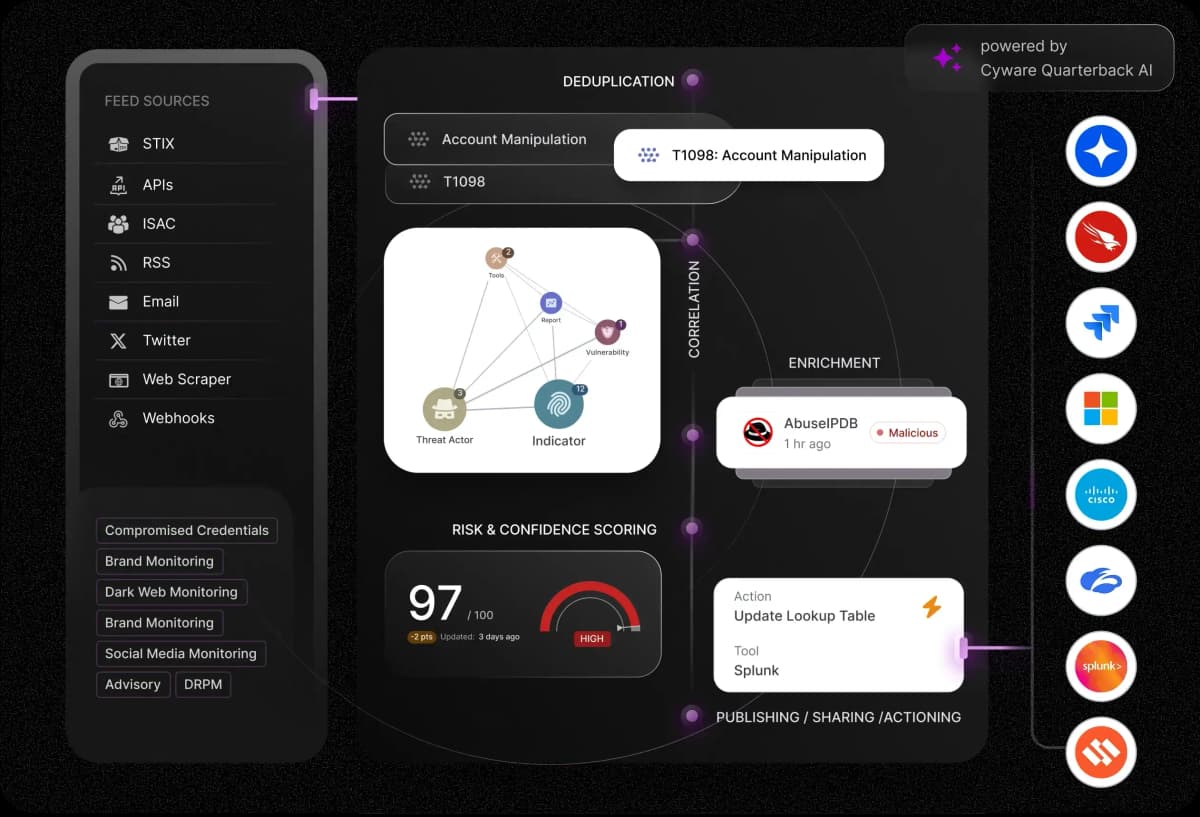
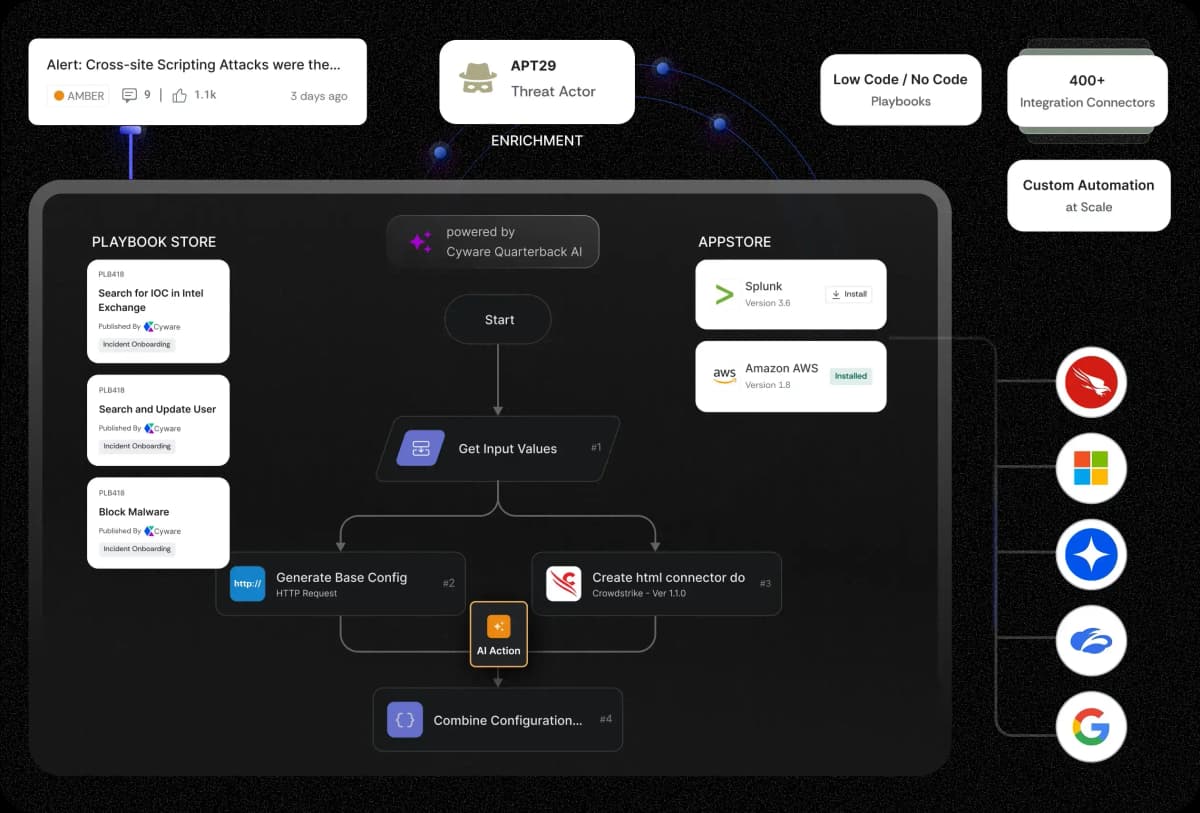
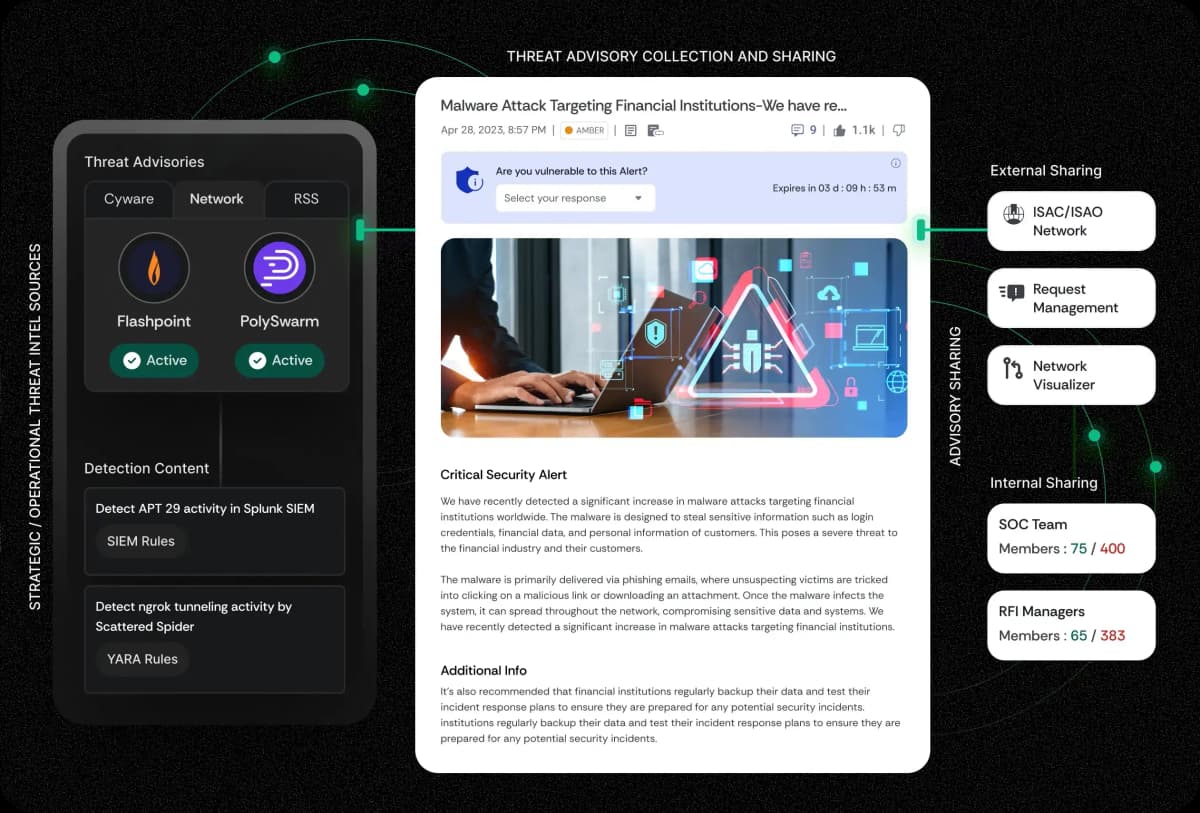


Delivering Threat Intelligence Actioning at Scale
Unmatched scalability, seamless collaboration, and real-time actioning.
15B+
Threat Intelligence Objects Ingested
30K+
Organizations Leverage the Value of the Cyware Platform
10M+
Actions Taken for Threat Mitigation
You're just One Platform
away from enhancing your organization’s security.
Request a demo now!