Go From a Threat-Informed to a Threat-Intelligence-Driven Program
Cyware Intel Exchange transforms raw threat intelligence into actionable defense.
With AI-powered workflows and seamless integrations, security teams can operationalize intelligence at scale and stay ahead of attackers.
15 Billion+
Threat Intelligence Objects Ingested
10 Million+
Actions Taken for Threat Mitigation
Why Threat Intel Platform Face Operationalization Challenge
Security teams are overwhelmed by massive volumes of data, causing alert fatigue and missed threats without automation and context.
Streamline Intelligence with Cyware Intel Exchange
Powered by AI and automation, and extended through the MCP Server, Cyware Intel Exchange enables end-to-end management of the threat intelligence lifecycle.
Automated Ingestion, De-duplication, and Normalization of Threat Data
Automated Format-Agnostic Ingestion
Pull intelligence from structured and unstructured sources like STIX, MISP, JSON, CSV, and email for faster threat visibility, powered by the MCP Server.
Automated De-duplication & Normalization
Remove duplicates and normalize to STIX 2.1 for clean, consistent, and actionable intelligence.
Quick Add Intel & Advanced Analysis
Use AI-powered entity extraction for fast imports and map threats to MITRE ATT&CK to uncover insights, powered by the MCP Server.
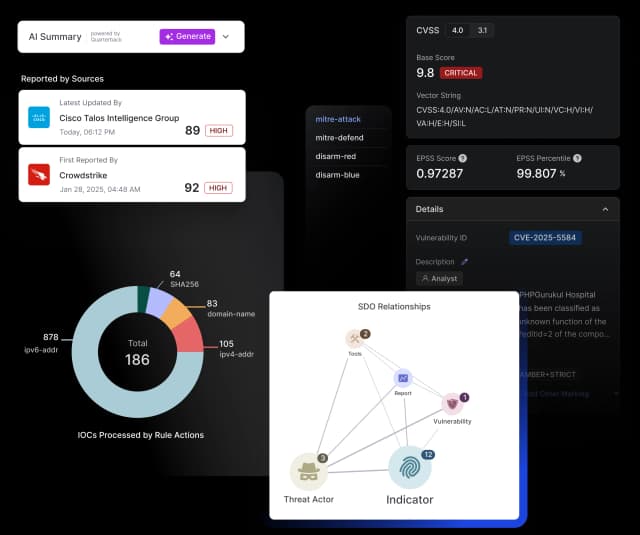
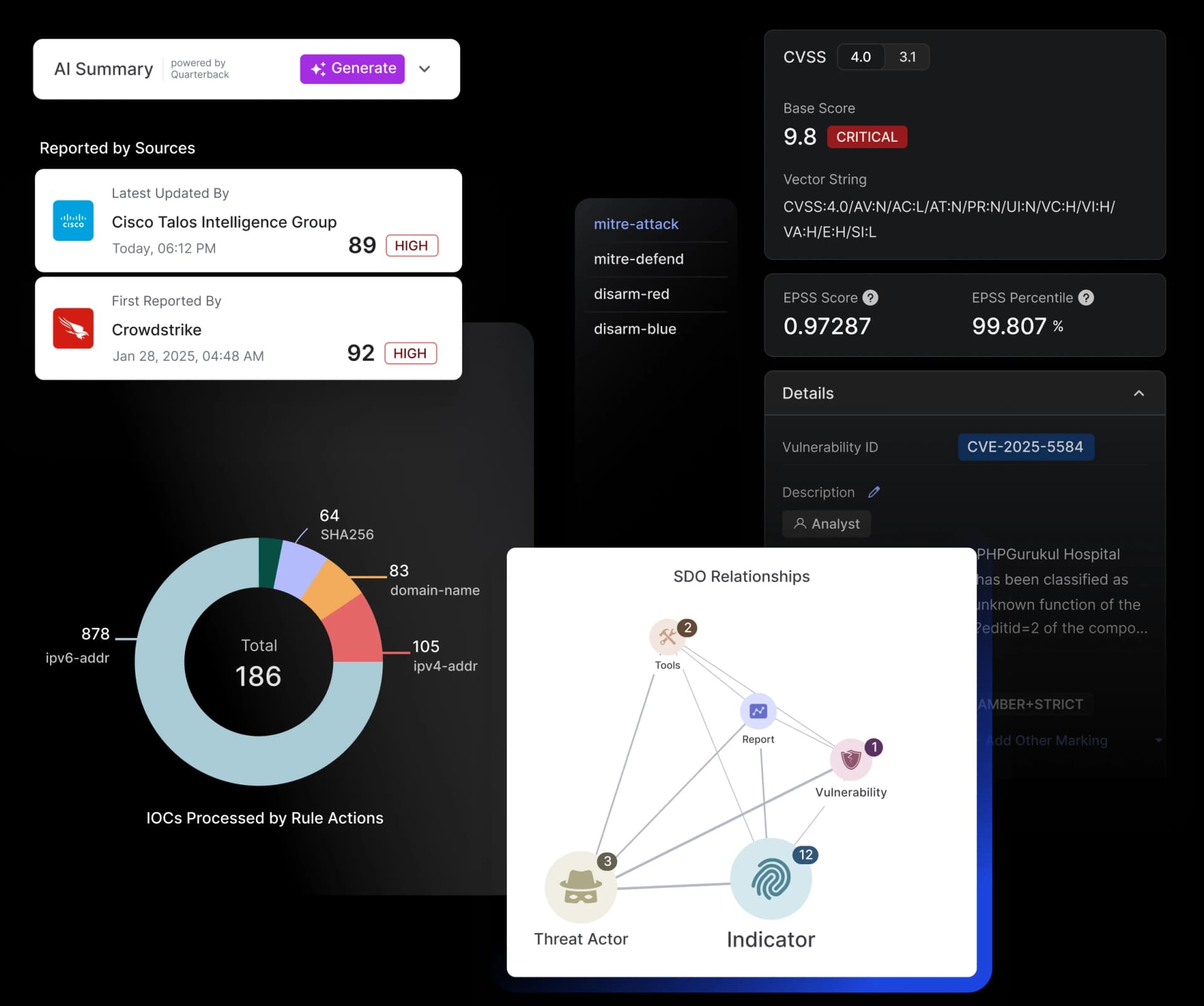
Automated Enrichment, Correlation & Risk Scoring for Advanced Analysis
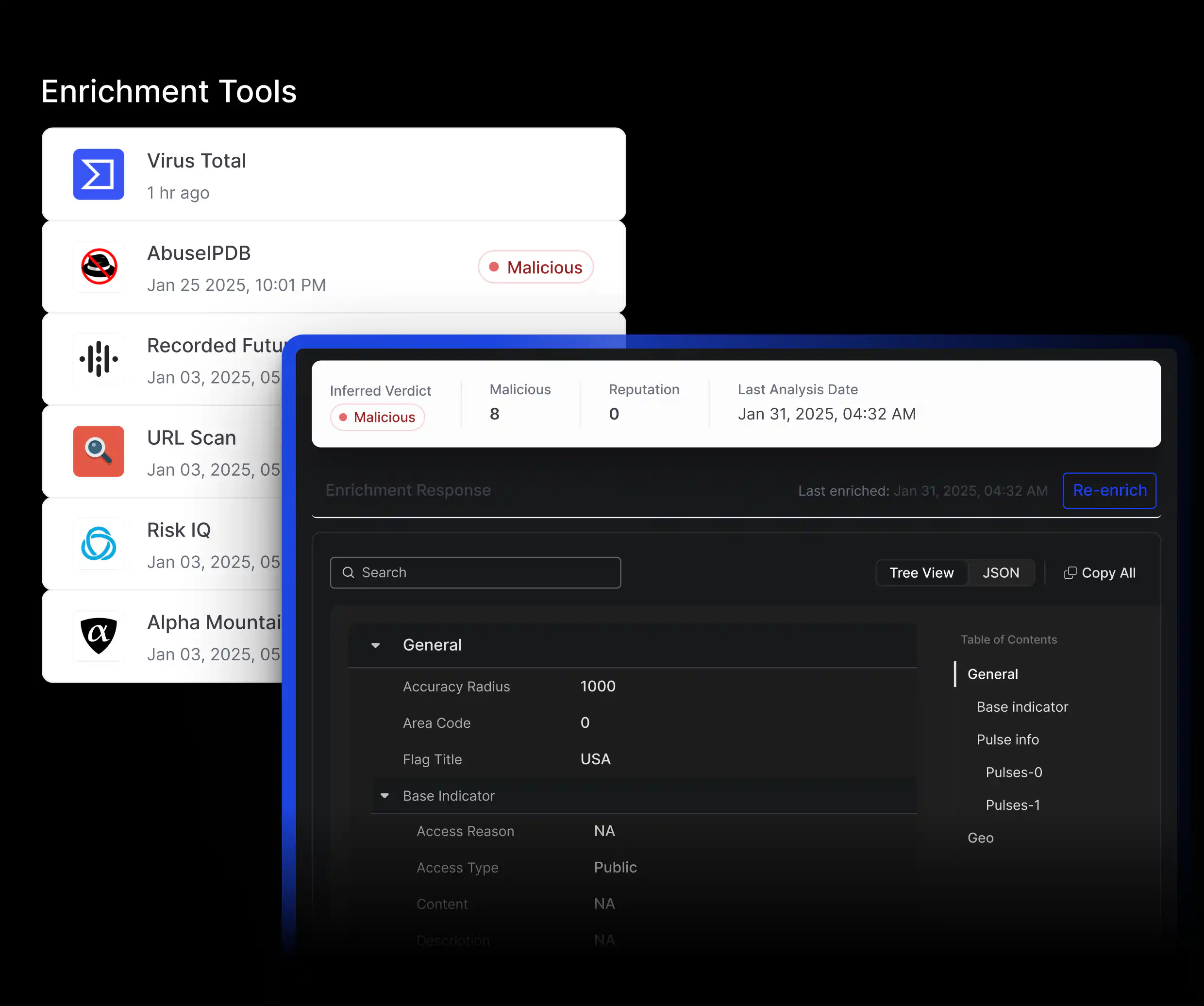
Pre-Built Connectors
Seamlessly enrich threat data from trusted sources like VirusTotal, Mandiant, PolySwarm, and more.
Customizable Risk Scoring Engine
Apply tailored threat prioritization based on source credibility, attributes, and enrichment to surface what matters most.
Threat Correlation & Analysis
Automatically correlate related indicators and uncover attack patterns to generate actionable insights quickly.
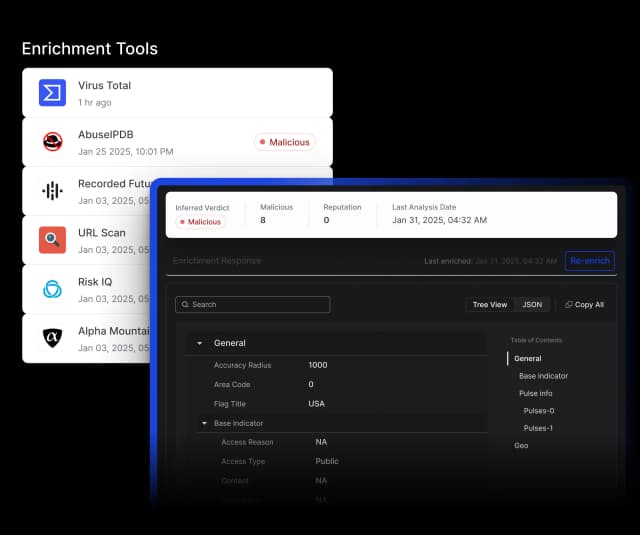
AI-Powered Workflows for Faster Threat Response
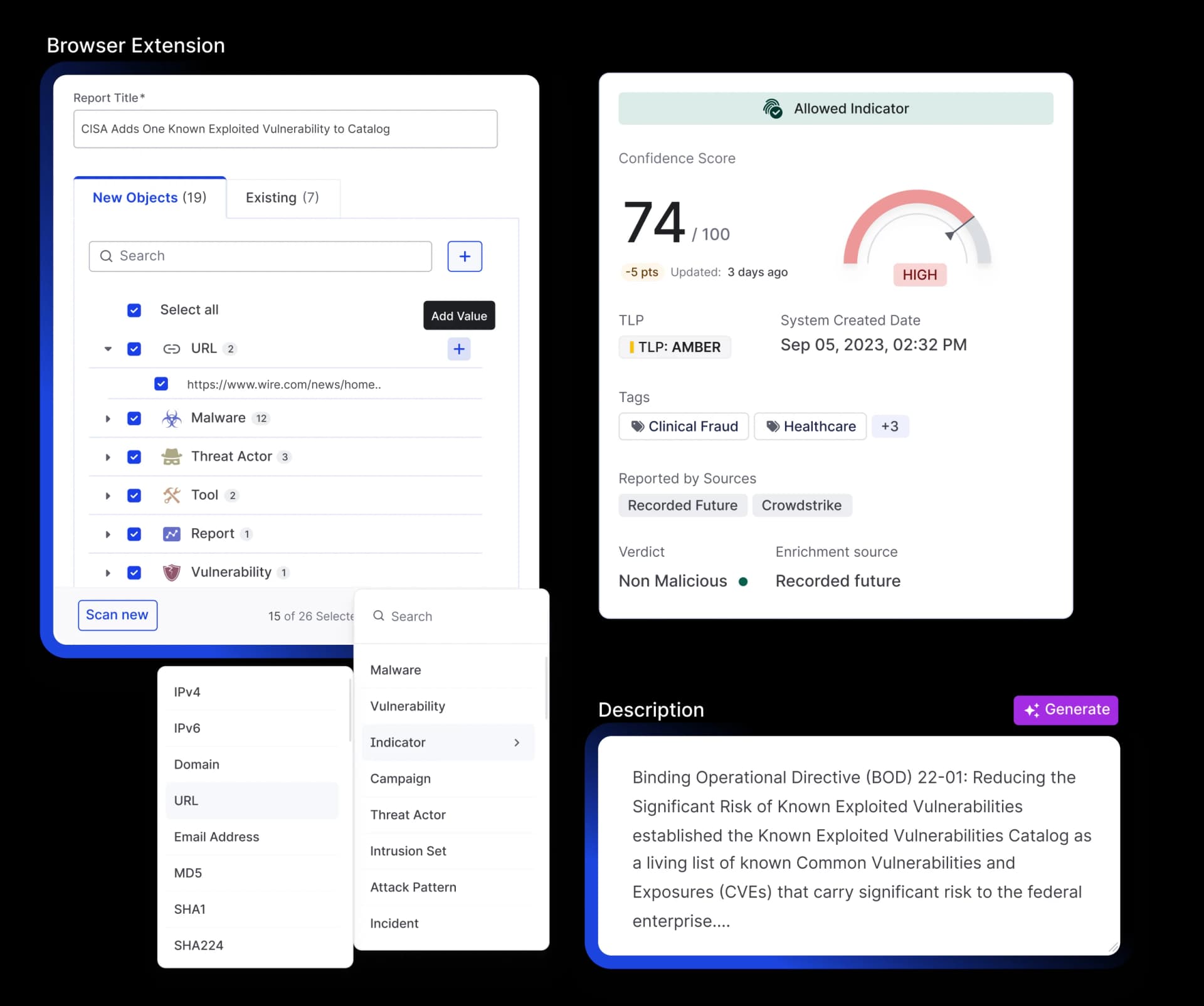
Quick Add & Report Summarization
Extract IOCs, IOBs, TTPs, threat actors, malware, and vulnerabilities while generating instant summaries for faster response.
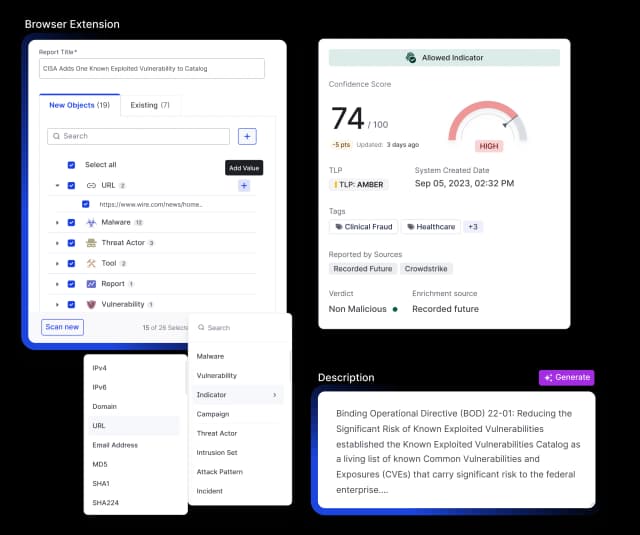
AI Threat Intel Crawler (Browser Plugin)
Convert web-based threat intelligence into structured data with enhanced parsing and sub-10-second response times.
Threat Intel Actioning via MCP Server
Query, summarize, and act on intel using natural language to accelerate triage, enrichment, and response workflows.
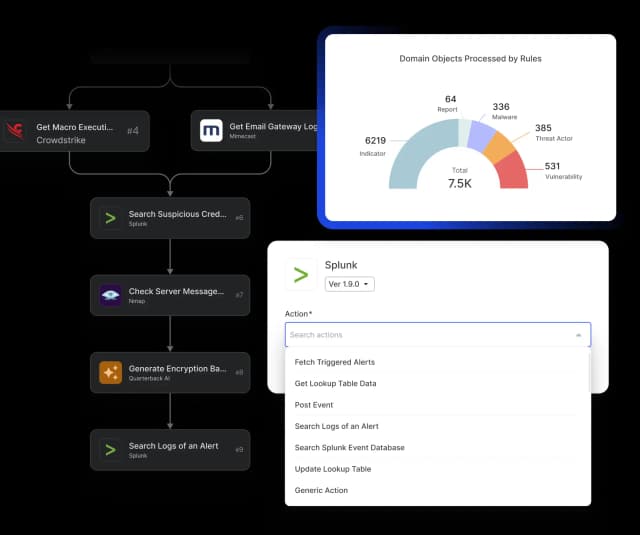
Automated Intelligence Actioning for Threat Response at Scale
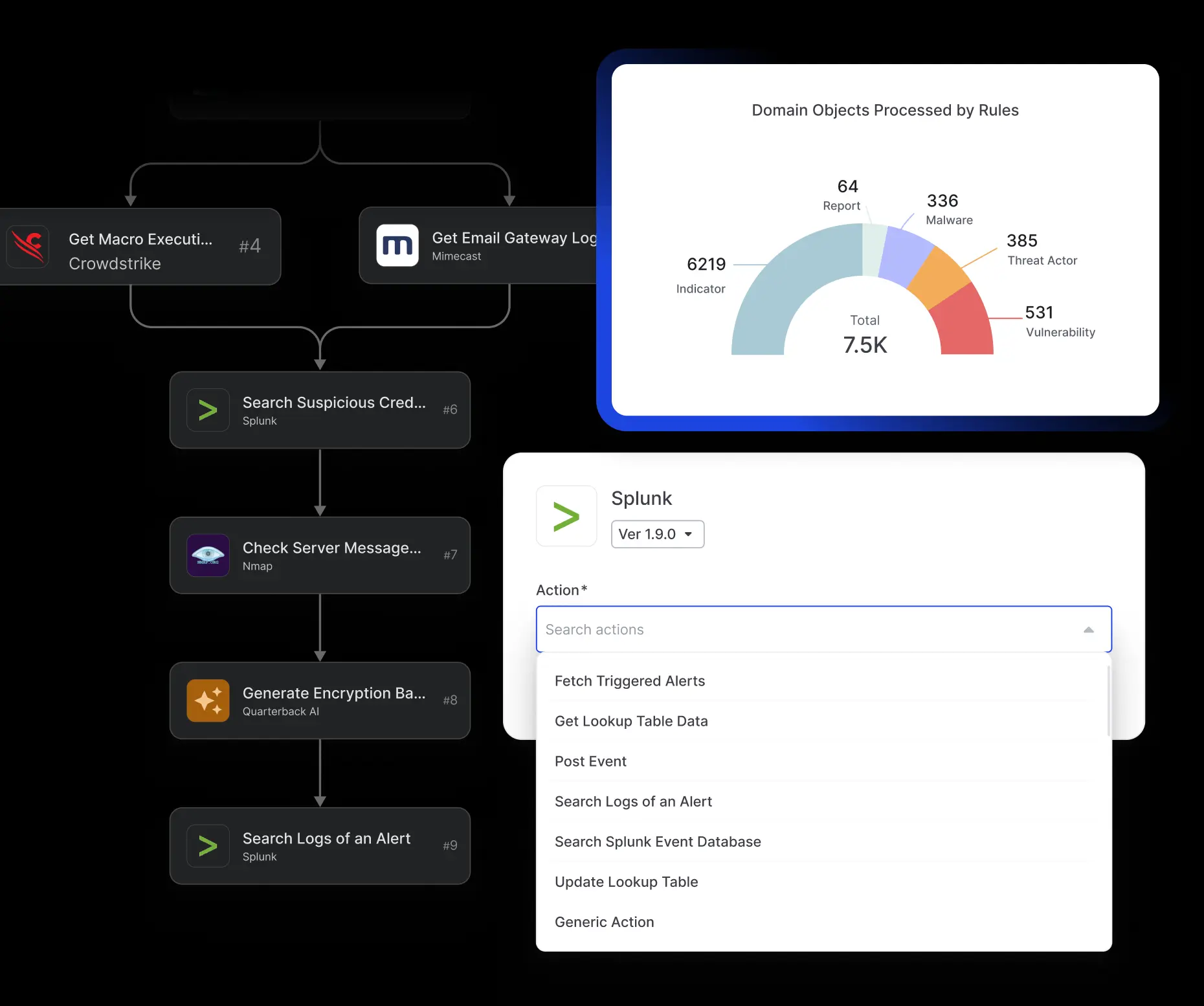
Rule Engine & Playbooks
Trigger automated workflows and response playbooks to accelerate triage and reduce manual effort.
Seamless Security Tool Integrations for Actioning
Push curated intelligence to SIEM, SOAR, EDR, and other platforms for faster response.
Sandboxing & Playbook Automation
Analyze suspicious files or URLs, hunt threats, generate actionable indicators, and automate end-to-end workflows with playbooks.
Cyware Intel Exchange is an advanced Threat Intelligence Platform (TIP) that automates the ingestion, de-duplication, enrichment, correlation, analysis, sharing, and actioning of threat data to help security teams respond faster and more effectively.
Explore All Our Offerings
Learn how Cyware is your go-to platform to unify, operationalize, respond to, and securely share threat intelligence.