The Incident Management Challenge
Security teams struggle to manage alerts, incidents, and threat intelligence in disconnected tools, causing slow threat investigations and operational delays.
How Cyware Respond Transforms SecOps
AI-powered incident management unifies security operations, threat intelligence, and vulnerability for faster, smarter threat response workflows.
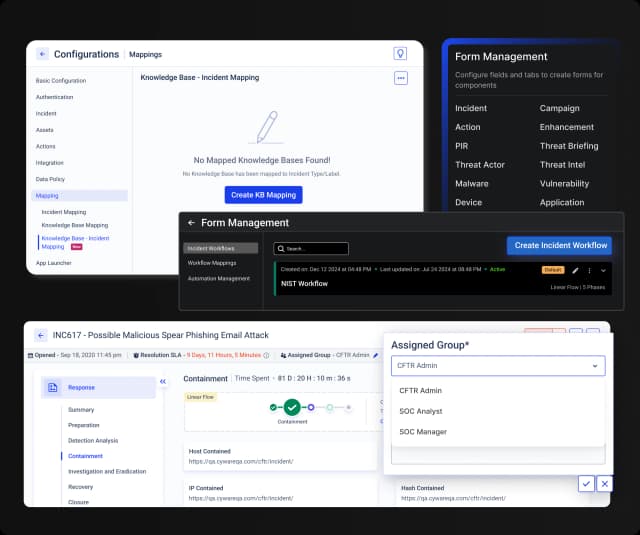
Unified Case Management & Collaboration
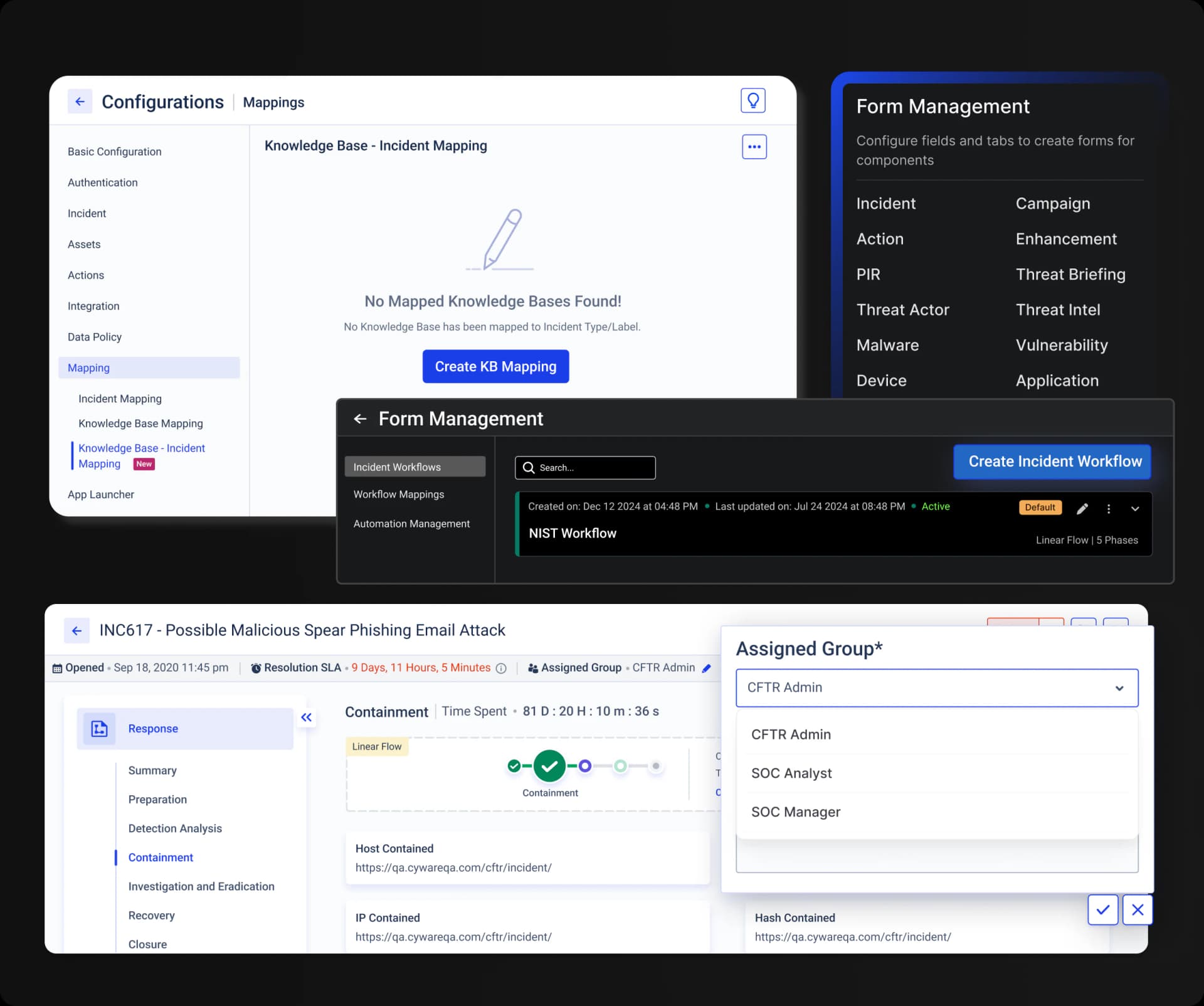
Customizable Workflows
Create custom forms and visual threat mapping to streamline response operations and enhance situational awareness.
Cross-Team Collaboration
Facilitate communication and coordination across internal and external teams from a single platform.
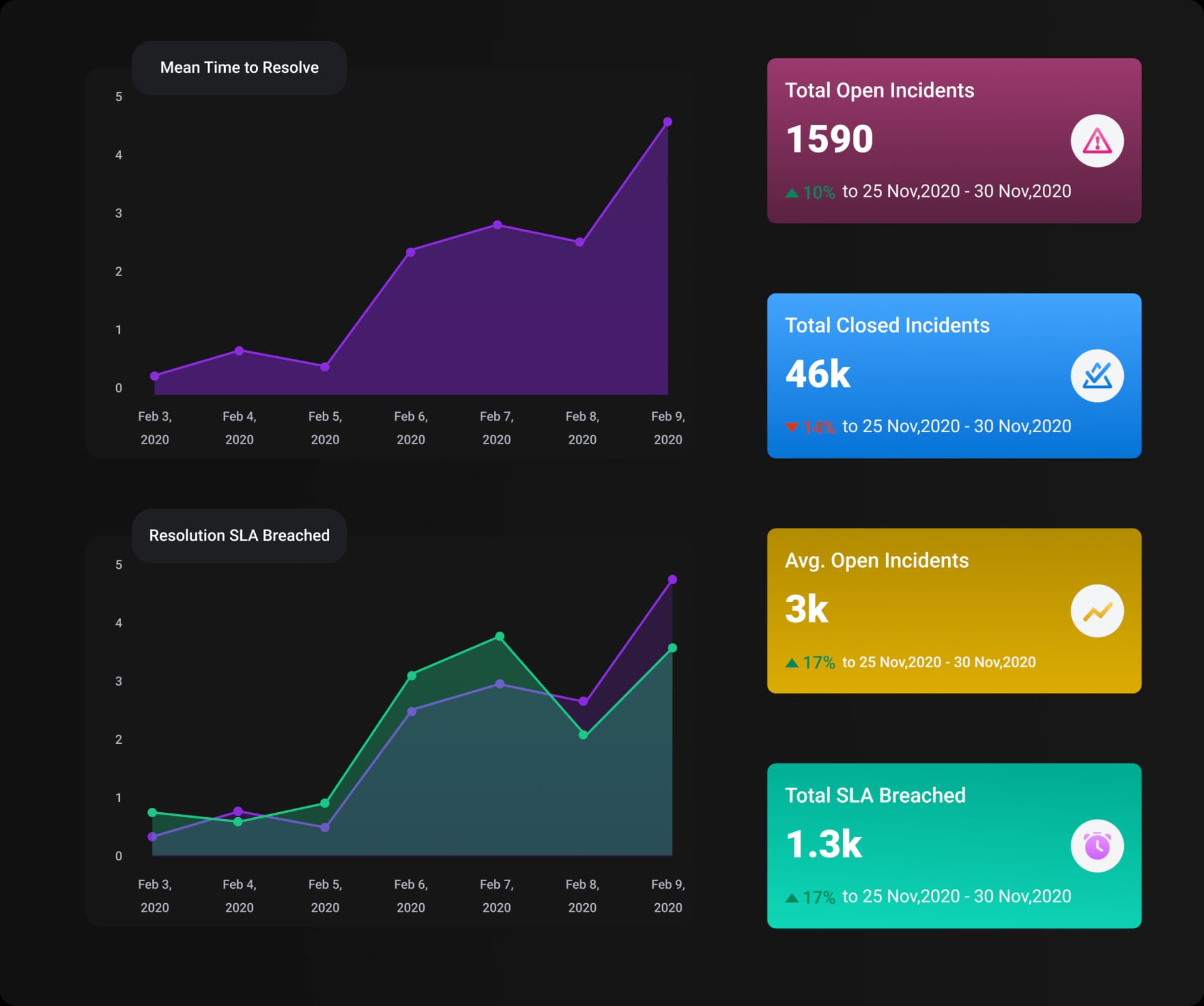
Metrics and Governance
Track key performance indicators (KPIs) like MTTD and MTTR with advanced reporting and auditing.
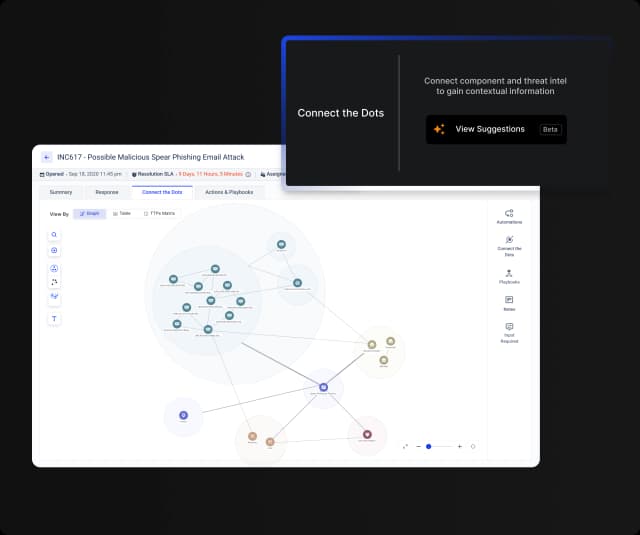
AI-Powered Threat Correlation & Analysis
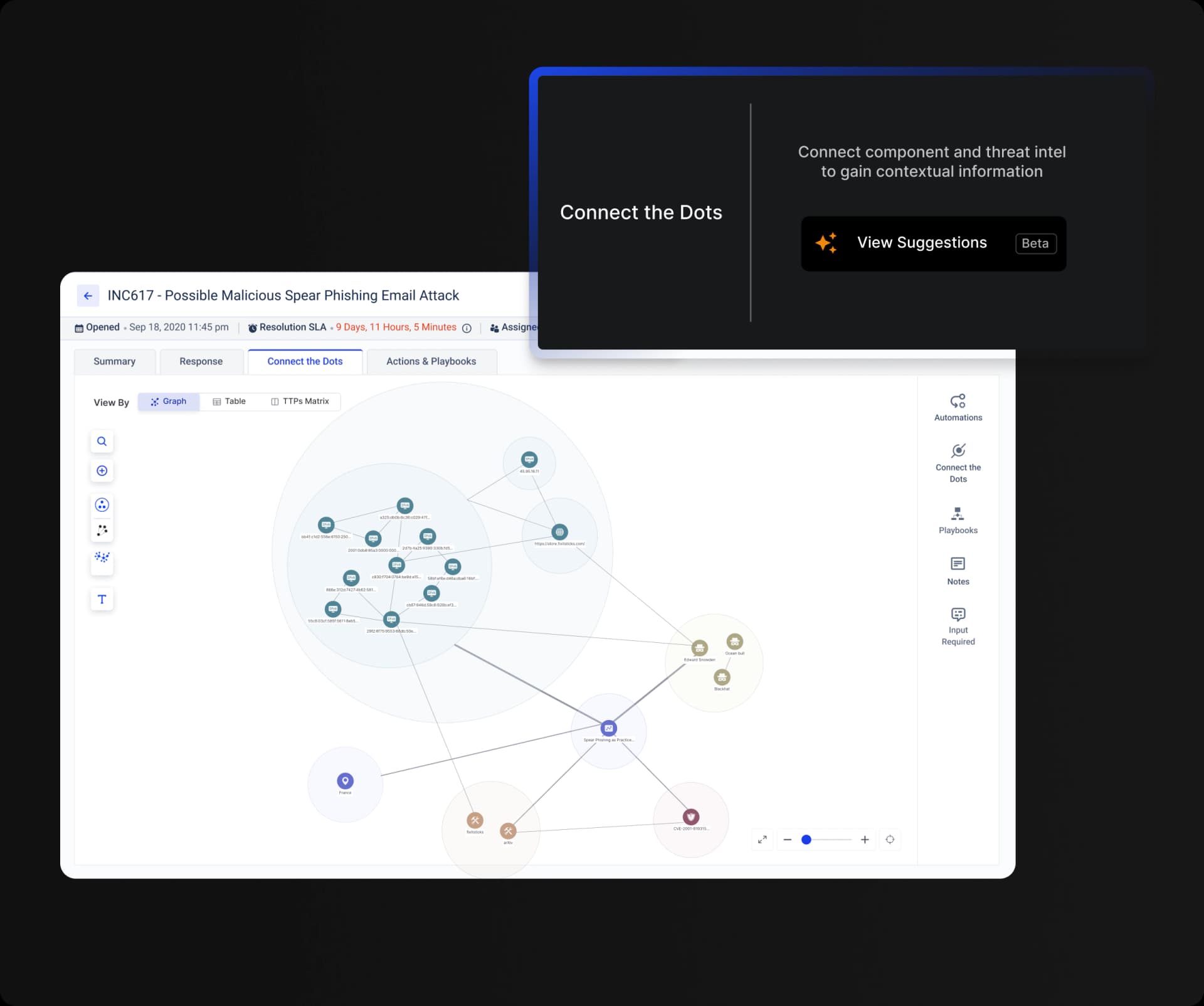
Connect the Dots
Visualize relationships between IOCs, TTPs, vulnerabilities, and assets for a complete threat picture.
AI Assist
Receive context-aware insights to uncover root causes and accelerate responses.
Proactive Threat Hunting
Use advanced analytics to identify and mitigate hidden threats before escalation.
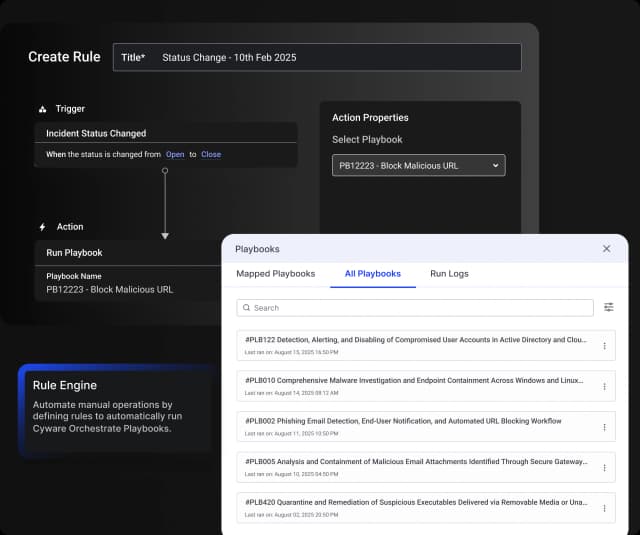
Hyper-Orchestration and Automation
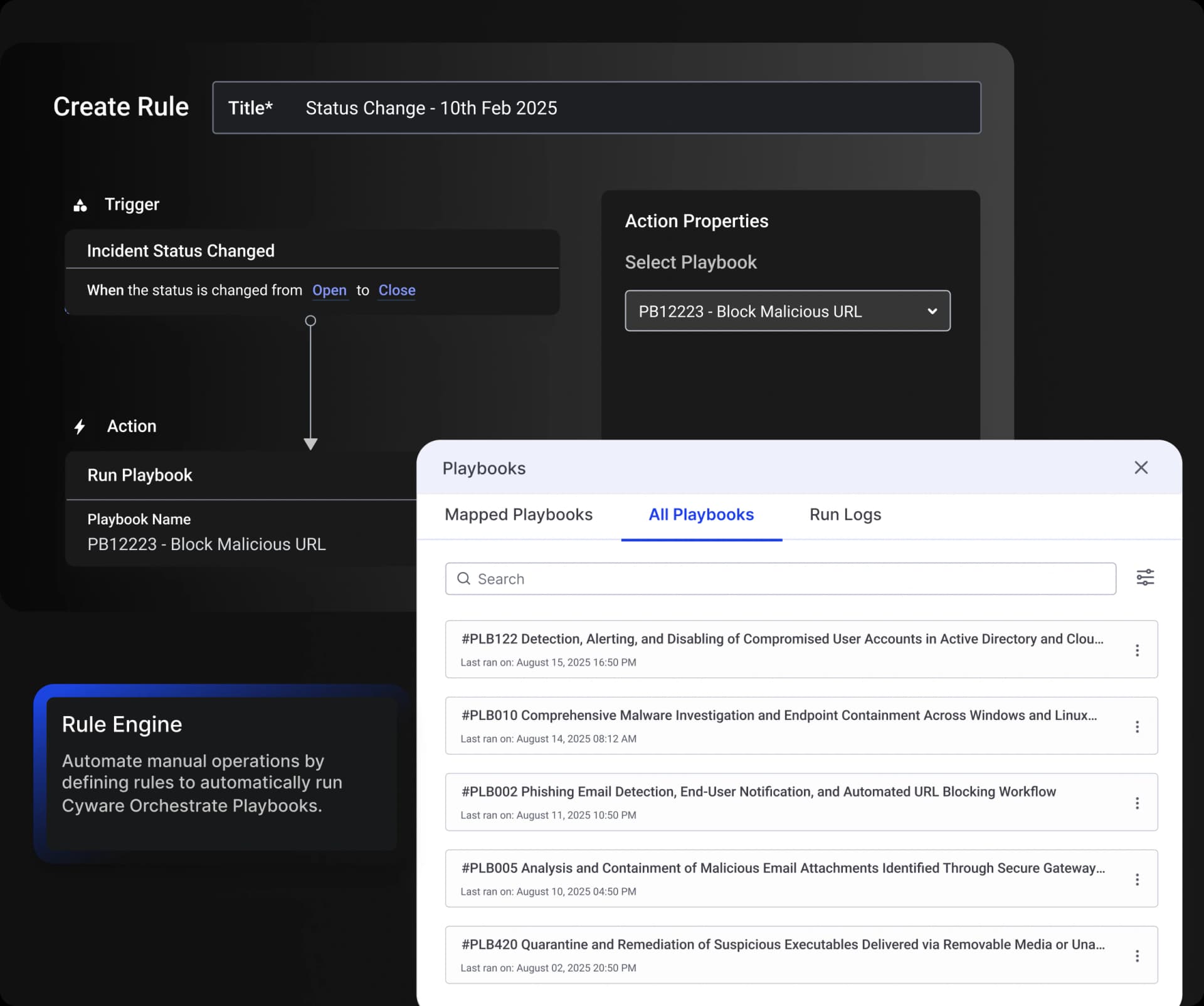
Integrated Playbooks
Associate playbooks with incident workflows to trigger automated actions at every stage.
Seamless Integrations
Plug-and-play integrations with 400+ security tools (SIEM, EDR, etc.) to unify your stack.
Automated Rule Engine
Define rules to automatically trigger workflows based on incident status or phase.
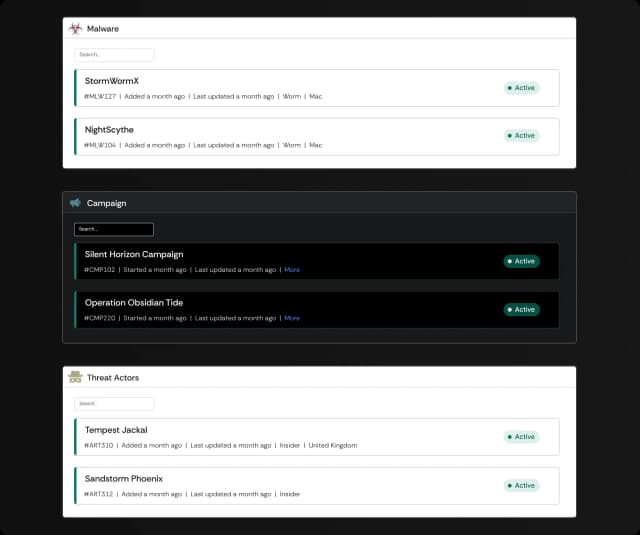
Comprehensive Threat Management
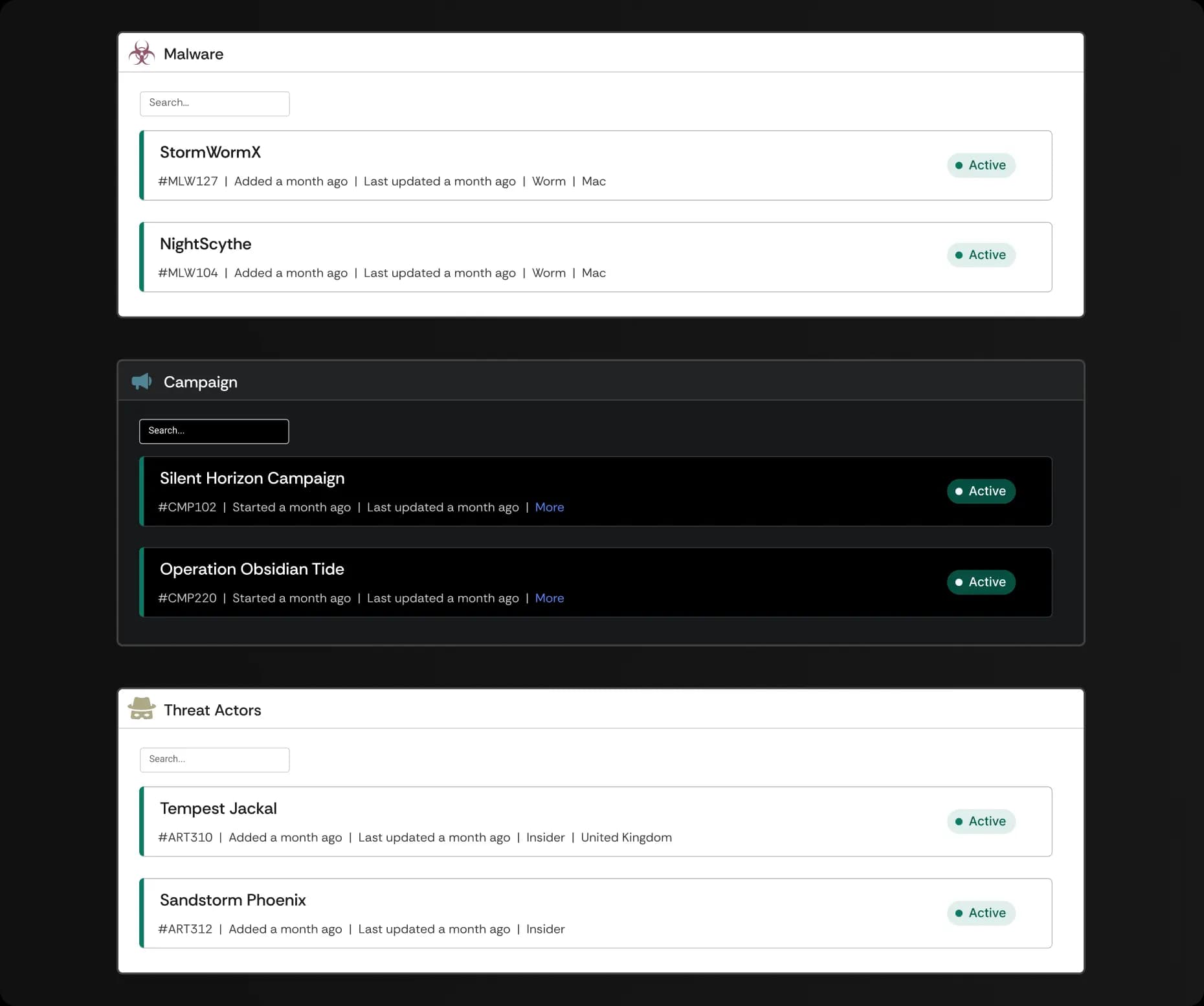
Vulnerability Database
Maintain a comprehensive database of vulnerabilities for proactive defense.
Malware Tracking
Monitor and control all malware-related activities, including mitigation and containment.
Threat Actor and Campaign Management
Track threat actors and group similar incidents into campaigns for enhanced monitoring.
Centralized Security Operations and Reporting
Multi-Tenant Dashboard
Centralize SLAs, KPIs, and incident management across business units or customers.
Analyst Workbench
Single interface for IP tracking, threat analysis, and investigations.
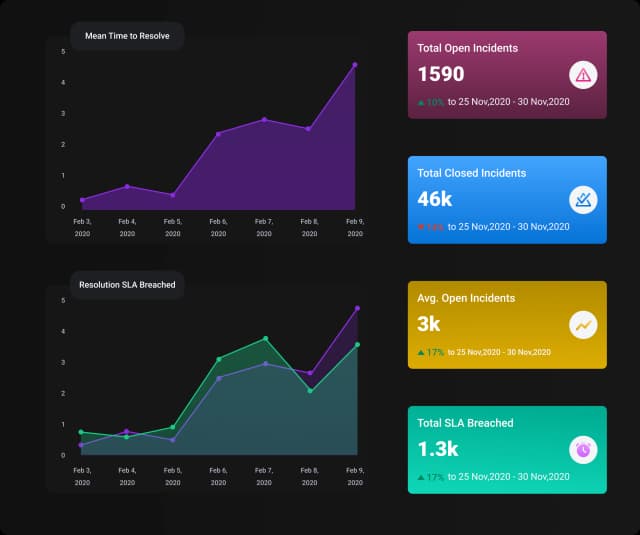
Customizable Dashboards
Track trends, metrics, and generate executive reports with built-in or custom widgets.
Cyware Respond is a comprehensive, AI-driven incident management platform that unifies threat intelligence, security orchestration, automation, and response (SOAR) into a single solution. It is designed to accelerate threat response and streamline security operations.
Explore All Our Offerings
Learn how Cyware is your go-to platform to unify, operationalize, respond to, and securely share threat intelligence.