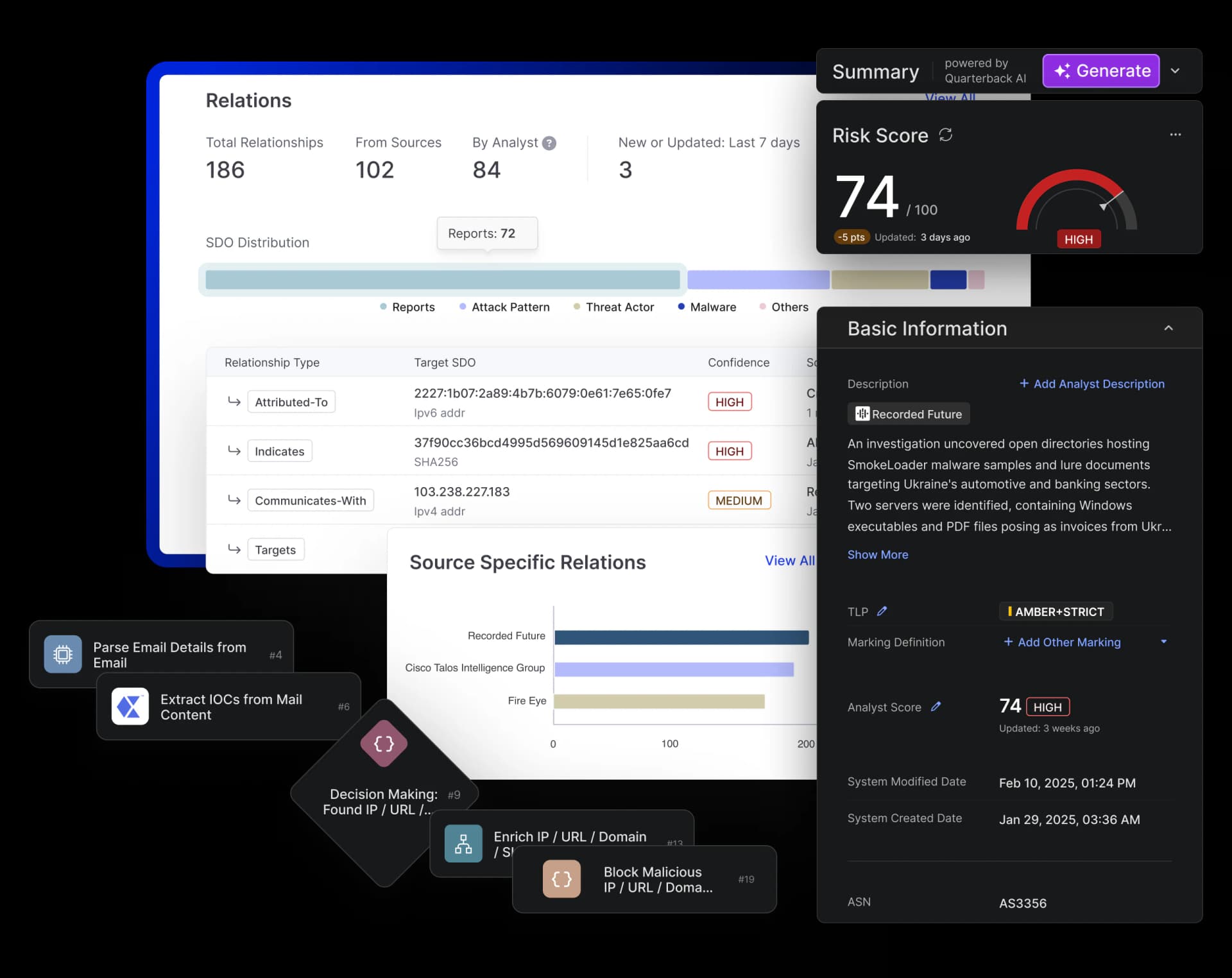
The Hidden Cost of Phishing Attacks
Phishing Emails Take Days to Detect and Mitigate
Even minor phishing alerts consume up to 30 minutes each, draining analyst efficiency and leaving SOCs exposed to targeted attacks, credential compromise, and potential ransomware.
Proactive Phishing Defense in Action with Cyware Orchestrate
Transforms phishing defense into strategic advantage, helping teams scale, detect targeted campaigns early, stop threats, and build lasting resilience.
Analyze Large Volumes of Phishing Emails
Save time and effectively respond to a large volume of phishing alerts with an automated response process, allowing analysts to focus on critical threats.
Track Targeted Attack Campaigns
IOC extraction and enrichment from multiple sources enable analysts to identify and counter the tactics and techniques used by threat actors.
Stop a variety of attacks at an early stage
By analyzing phishing throughout the full attack lifecycle, the playbook helps block actors attempting to infiltrate networks and deploy exploits.
Going Beyond Incident Investigation
The playbook not only resolves phishing threats but captures lessons to build long-term controls, strengthening defense against future attacks.
Analyze Large Volumes of Phishing Emails
Save time and effectively respond to a large volume of phishing alerts with an automated response process, allowing analysts to focus on critical threats.
Track Targeted Attack Campaigns
IOC extraction and enrichment from multiple sources enable analysts to identify and counter the tactics and techniques used by threat actors.
Stop a variety of attacks at an early stage
By analyzing phishing throughout the full attack lifecycle, the playbook helps block actors attempting to infiltrate networks and deploy exploits.
Going Beyond Incident Investigation
The playbook not only resolves phishing threats but captures lessons to build long-term controls, strengthening defense against future attacks.