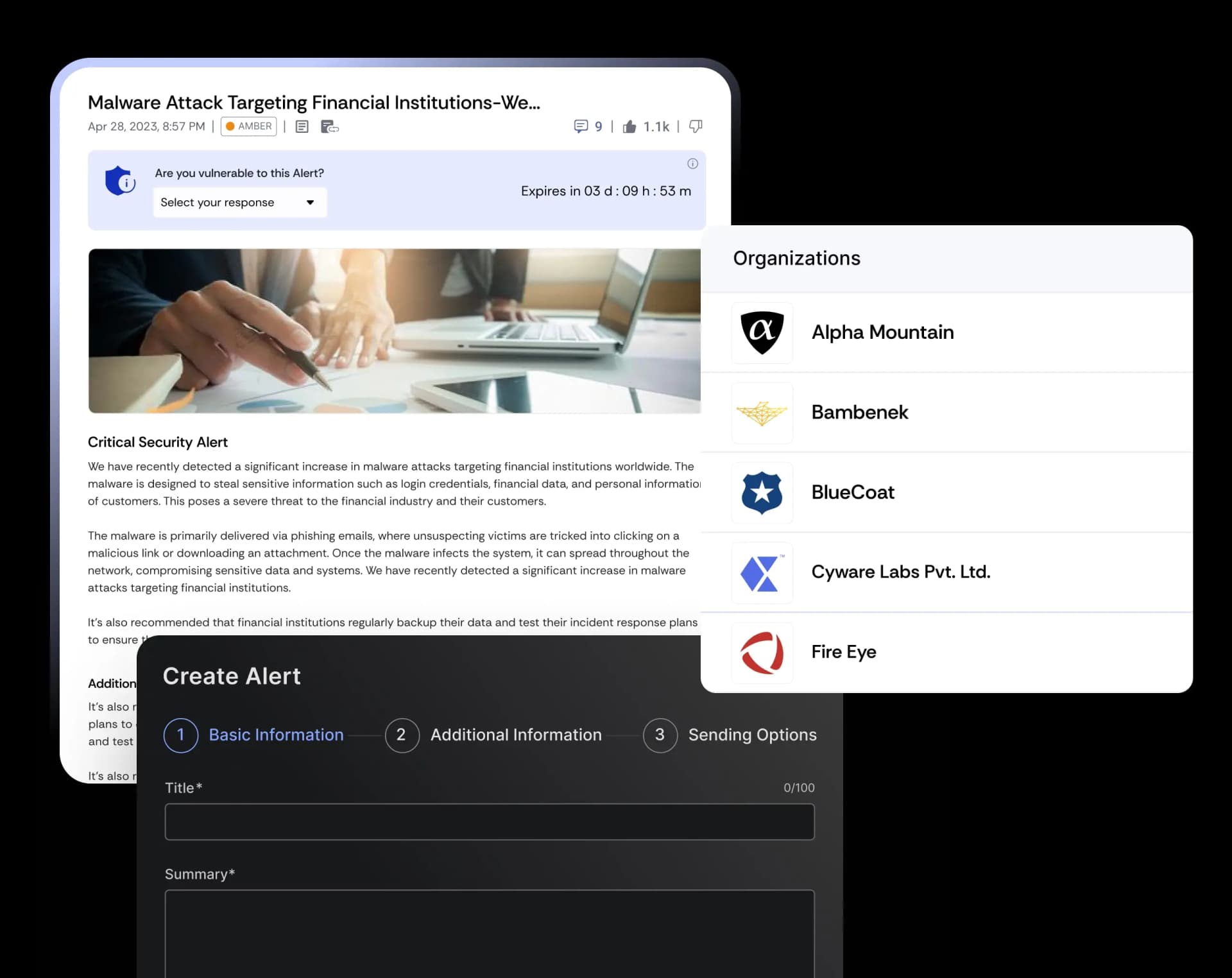
The Collaboration Gap in Threat Intelligence Sharing
Traditional Threat Intelligence Sharing Methods Aren’t Built for Real-Time Defense
Legacy systems can’t keep up with fast-moving threats, lack actionable context, and end up relying on manual efforts to turn alerts into defenses.
Streamline Threat Sharing and Collaboration Across Your ISAC
Cyware enables you to transform your ISAC into a collective defense network with real-time intelligence and secure collaboration.
Federated Hub-and-Spoke Networks
Build scalable sharing models where hubs curate and distribute intel while members contribute sightings and feedback, creating a continuous loop of enriched intelligence.
Real-Time, Enriched Threat Visibility
Deliver curated, sector-specific intel to every member instantly. Indicators are pre-scored, enriched with context, and mapped to campaigns, allowing ISAC members to act without delay
End-to-End Automation
Eliminate manual bottlenecks by automating ingestion, enrichment, and distribution. High-confidence indicators flow directly into members’ SIEM, SOAR, and EDR tools for instant defense.
Analyst-to-Analyst Collaboration
Enable secure communication channels where members co-investigate, share detection rules, and coordinate joint responses, strengthening sector-wide resilience and collective defense.
Federated Hub-and-Spoke Networks
Build scalable sharing models where hubs curate and distribute intel while members contribute sightings and feedback, creating a continuous loop of enriched intelligence.
Real-Time, Enriched Threat Visibility
Deliver curated, sector-specific intel to every member instantly. Indicators are pre-scored, enriched with context, and mapped to campaigns, allowing ISAC members to act without delay
End-to-End Automation
Eliminate manual bottlenecks by automating ingestion, enrichment, and distribution. High-confidence indicators flow directly into members’ SIEM, SOAR, and EDR tools for instant defense.
Analyst-to-Analyst Collaboration
Enable secure communication channels where members co-investigate, share detection rules, and coordinate joint responses, strengthening sector-wide resilience and collective defense.
operational defense centers. By automating intel ingestion, enrichment, and distribution, Cyware ensures ISAC members receive actionable insights immediately. Cyware also enables secure analyst-to-analyst collaboration, allowing ISACs to coordinate incident response in real-time and accelerate collective defense across entire sectors.