The Malware Sandboxing Challenge in Threat Intelligence
No Sandbox at All or a
Disconnected One That Isn’t Useful
Threat intelligence platforms relying on external sandboxes cause fragmented workflows, delays, and overhead leaving behavioral insights siloed and slowing investigations and response.
With Cyware, You Get Native Sandboxing for Smarter Investigations
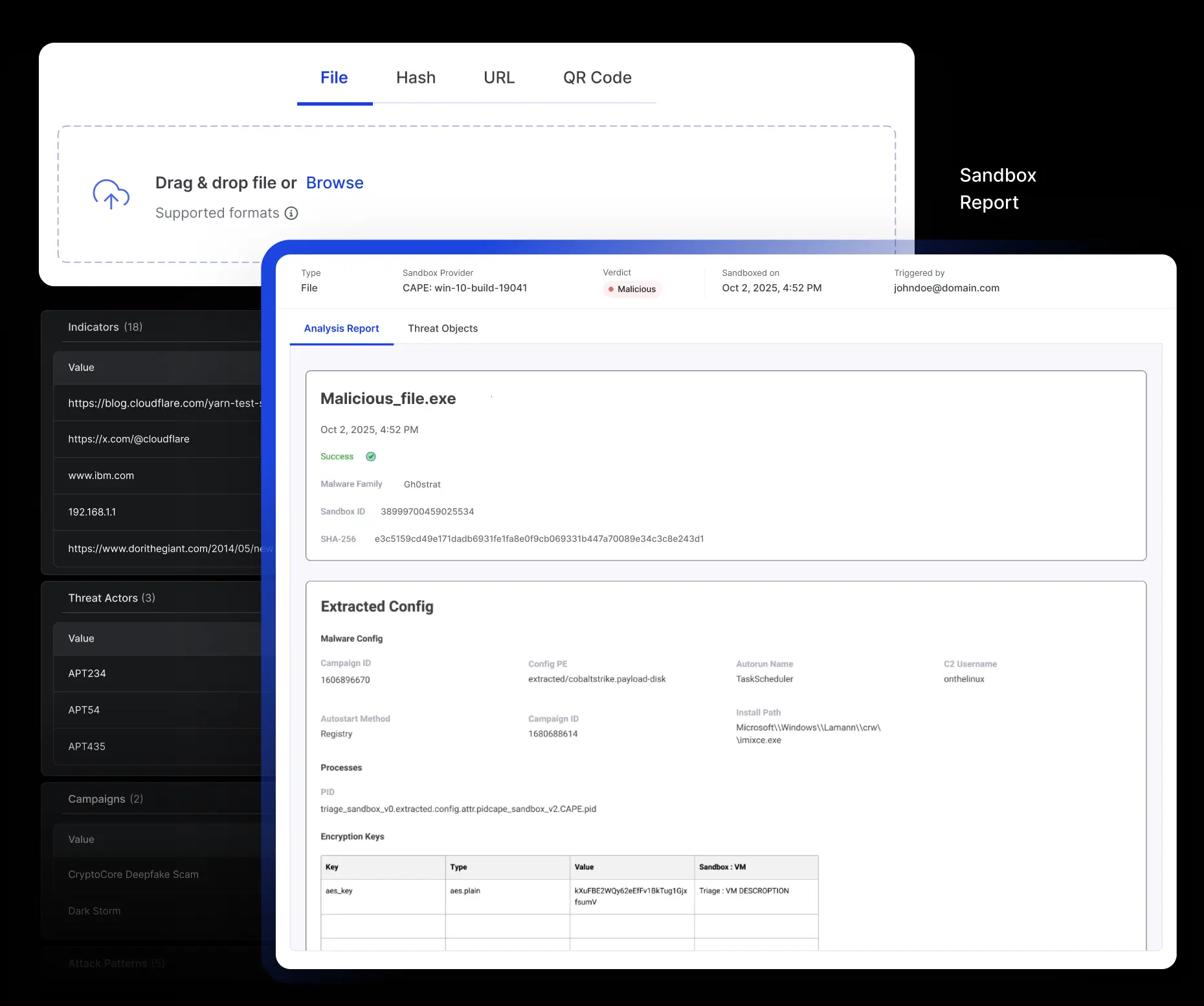
Cyware Sandbox Service delivers multi-engine malware detonation within Intel Exchange Private Communities for full control, privacy, and instant enrichment.
Multi-Engine Analysis in a Click
Leverage industry-leading CAPE (Configuration and Payload Extraction) and Triage sandbox engines to analyze static and behavioral traits across Windows, Linux, and Android environments.
Rich Artifact Output
Each sandbox session yields downloadable artifacts, including PCAP files, dropped files, memory dumps, JARM signatures, video recordings of detonation, and full HTML reports.
IOC Extraction & TTP Mapping
Automatically extract malware hashes and network IOCs (IPv4, domains, URLs) during the analysis, with attack patterns mapped to MITRE ATT&CK TTPs.
Malware Detonation
All sandbox analysis is performed inside Private Communities within Cyware Intel Exchange, ensuring zero third-party exposure and total data control.
Multi-Engine Analysis in a Click
Leverage industry-leading CAPE (Configuration and Payload Extraction) and Triage sandbox engines to analyze static and behavioral traits across Windows, Linux, and Android environments.
Rich Artifact Output
Each sandbox session yields downloadable artifacts, including PCAP files, dropped files, memory dumps, JARM signatures, video recordings of detonation, and full HTML reports.
IOC Extraction & TTP Mapping
Automatically extract malware hashes and network IOCs (IPv4, domains, URLs) during the analysis, with attack patterns mapped to MITRE ATT&CK TTPs.
Malware Detonation
All sandbox analysis is performed inside Private Communities within Cyware Intel Exchange, ensuring zero third-party exposure and total data control.