The Ransomware Challenge for Organizations
Escalating Frequency, Rising Impact
Ransomware is no longer a rare event, it’s a constant and evolving threat with attacks growing in scale and sophistication, causing severe downtime, financial loss, and reputational damage.
Strengthen Your Cyber Defenses with Cyware
Detect ransomware early, validate alerts with contextual intelligence, and contain threats instantly.
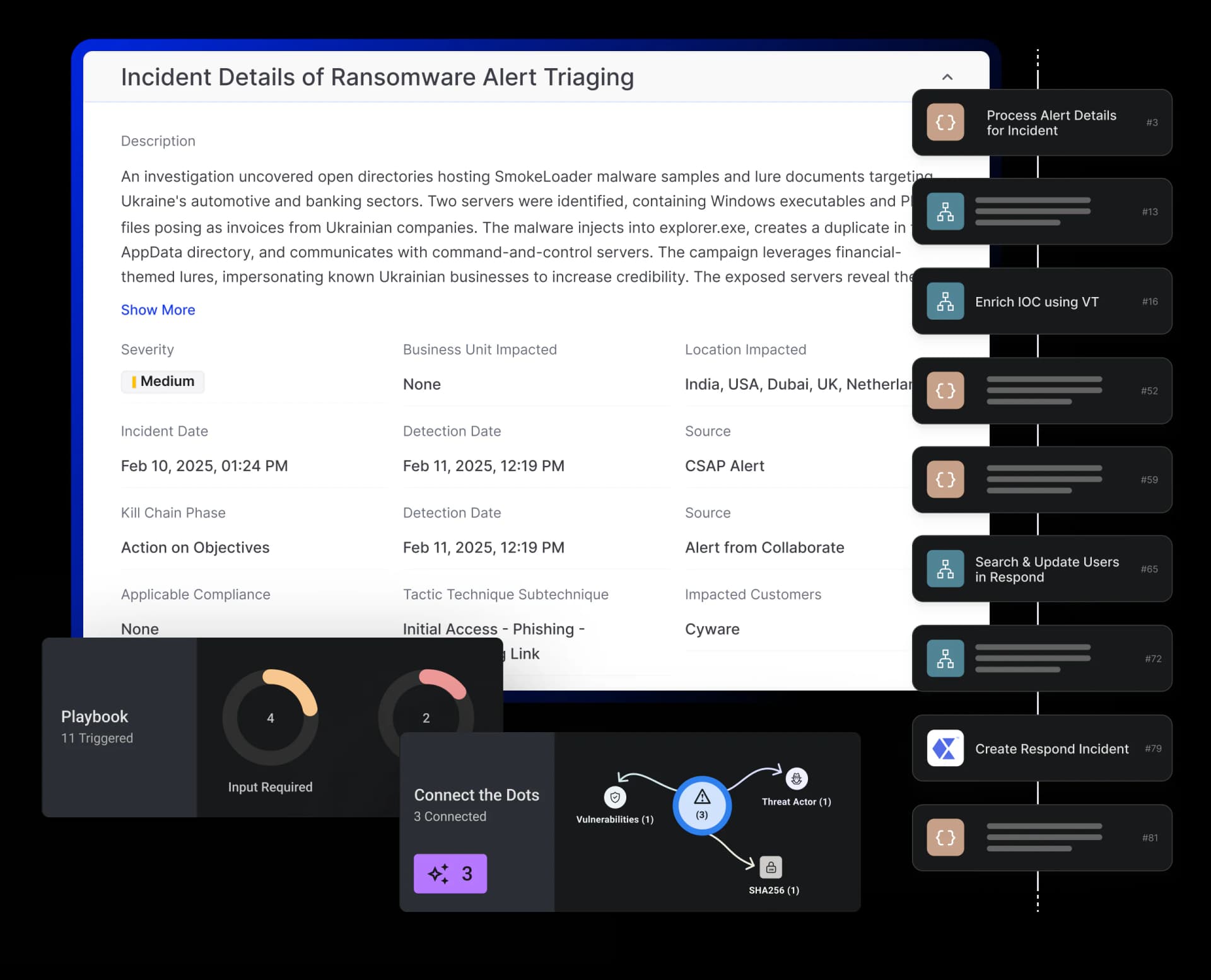
Automated Incident Triage
Automatically create and investigate ransomware alerts from your EDR. Enrich IOCs with threat intelligence and correlate data to validate threats thereby minimizing manual work and speeding up analysis.
Intelligence-Driven Enrichment
Enrich IOCs with premium and open-source intelligence to uncover affected assets, users, and potential blast radius, giving analysts full situational awareness.
Rapid, Decisive Containment
Quarantine malicious hashes and isolate affected assets instantly. Automated containment prevents ransomware spread, reducing the scope and impact of attacks.
Standardized, Auditable Response
Execute consistent, playbook-driven response workflows for every ransomware incident. Improve accountability, ensure compliance, and continuously refine defenses.
Automated Incident Triage
Automatically create and investigate ransomware alerts from your EDR. Enrich IOCs with threat intelligence and correlate data to validate threats thereby minimizing manual work and speeding up analysis.
Intelligence-Driven Enrichment
Enrich IOCs with premium and open-source intelligence to uncover affected assets, users, and potential blast radius, giving analysts full situational awareness.
Rapid, Decisive Containment
Quarantine malicious hashes and isolate affected assets instantly. Automated containment prevents ransomware spread, reducing the scope and impact of attacks.
Standardized, Auditable Response
Execute consistent, playbook-driven response workflows for every ransomware incident. Improve accountability, ensure compliance, and continuously refine defenses.